5.2: Persuasion- So Easily Fooled
- Last updated
- Save as PDF
- Page ID
- 11947
California State University, Fresno
This module introduces several major principles in the process of persuasion. It offers an overview of the different paths to persuasion. It then describes how mindless processing makes us vulnerable to undesirable persuasion and some of the “tricks” that may be used against us.
learning objectives
- Recognize the difference between the central and peripheral routes to persuasion.
- Understand the concepts of trigger features, fixed action patterns, heuristics, and mindless thinking, and how these processes are essential to our survival but, at the same time, leave us vulnerable to exploitation.
- Understand some common “tricks” persuasion artists may use to take advantage of us.
- Use this knowledge to make you less susceptible to unwanted persuasion.
Introduction
Have you ever tried to swap seats with a stranger on an airline? Ever negotiated the price of a car? Ever tried to convince someone to recycle, quit smoking, or make a similar change in health behaviors? If so, you are well versed with how persuasion can show up in everyday life.
Persuasion has been defined as “the process by which a message induces change in beliefs, attitudes, or behaviors” (Myers, 2011). Persuasion can take many forms. It may, for example, differ in whether it targets public compliance or private acceptance, is short-term or long-term, whether it involves slowly escalating commitments or sudden interventions and, most of all, in the benevolence of its intentions. When persuasion is well-meaning, we might call it education. When it is manipulative, it might be called mind control (Levine, 2003).
Whatever the content, however, there is a similarity to the form of the persuasion process itself. As the advertising commentator Sid Bernstein once observed, “Of course, you sell candidates for political office the same way you sell soap or sealing wax or whatever; because, when you get right down to it, that’s the only way anything is sold” (Levine, 2003).
Persuasion is one of the most studied of all social psychology phenomena. This module provides an introduction to several of its most important components.

Two Paths to Persuasion
Persuasion theorists distinguish between the central and peripheral routes to persuasion (Petty & Cacioppo, 1986). The central route employs direct, relevant, logical messages. This method rests on the assumption that the audience is motivated, will think carefully about what is presented, and will react on the basis of your arguments. The central route is intended to produce enduring agreement. For example, you might decide to vote for a particular political candidate after hearing her speak and finding her logic and proposed policies to be convincing.
The peripheral route, on the other hand, relies on superficial cues that have little to do with logic. The peripheral approach is the salesman’s way of thinking. It requires a target who isn’tthinking carefully about what you are saying. It requires low effort from the target and often exploits rule-of-thumb heuristics that trigger mindless reactions (see below). It may be intended to persuade you to do something you do not want to do and might later be sorry you did. Advertisements, for example, may show celebrities, cute animals, beautiful scenery, or provocative sexual images that have nothing to do with the product. The peripheral approach is also common in the darkest of persuasion programs, such as those of dictators and cult leaders. Returning to the example of voting, you can experience the peripheral route in action when you see a provocative, emotionally charged political advertisement that tugs at you to vote a particular way.
Triggers and Fixed Action Patterns
The central route emphasizes objective communication of information. The peripheral route relies on psychological techniques. These techniques may take advantage of a target’s not thinking carefully about the message. The process mirrors a phenomenon in animal behavior known as fixed action patterns (FAPs). These are sequences of behavior that occur in exactly the same fashion, in exactly the same order, every time they’re elicited. Cialdini (2008) compares it to a prerecorded tape that is turned on and, once it is, always plays to its finish. He describes it is as if the animal were turning on a tape recorder (Cialdini, 2008). There is the feeding tape, the territorial tape, the migration tape, the nesting tape, the aggressive tape—each sequence ready to be played when a situation calls for it.
In humans fixed action patterns include many of the activities we engage in while mentally on "auto-pilot." These behaviors are so automatic that it is very difficult to control them. If you ever feed a baby, for instance, nearly everyone mimics each bite the baby takes by opening and closing their own mouth! If two people near you look up and point you will automatically look up yourself. We also operate in a reflexive, non-thinking way when we make many decisions. We are more likely, for example, to be less critical about medical advice dispensed from a doctor than from a friend who read an interesting article on the topic in a popular magazine.
A notable characteristic of fixed action patterns is how they are activated. At first glance, it appears the animal is responding to the overall situation. For example, the maternal tape appears to be set off when a mother sees her hungry baby, or the aggressive tape seems to be activated when an enemy invades the animal’s territory. It turns out, however, that the on/off switch may actually be controlled by a specific, minute detail of the situation—maybe a sound or shape or patch of color. These are the hot buttons of the biological world—what Cialdini refers to as “trigger features” and biologists call “releasers.”

Humans are not so different. Take the example of a study conducted on various ways to promote a campus bake sale for charity (Levine, 2003). Simply displaying the cookies and other treats to passersby did not generate many sales (only 2 out of 30 potential customers made a purchase). In an alternate condition, however, when potential customers were asked to "buy a cookie for a good cause" the number rose to 12 out of 30. It seems that the phrase "a good cause" triggered a willingness to act. In fact, when the phrase "a good cause" was paired with a locally-recognized charity (known for its food-for-the-homeless program) the numbers held steady at 14 out of 30. When a fictional good cause was used instead (the make believe "Levine House") still 11 out of 30 potential customers made purchases and not one asked about the purpose or nature of the cause. The phrase "for a good cause" was an influential enough hot button that the exact cause didn't seem to matter.
The effectiveness of peripheral persuasion relies on our frequent reliance on these sorts of fixed action patterns and trigger features. These mindless, rules-of-thumb are generally effective shortcuts for coping with the overload of information we all must confront. They serve as heuristics—mental shortcuts-- that enable us to make decisions and solve problems quickly and efficiently. They also, however, make us vulnerable to uninvited exploitation through the peripheral route of persuasion.
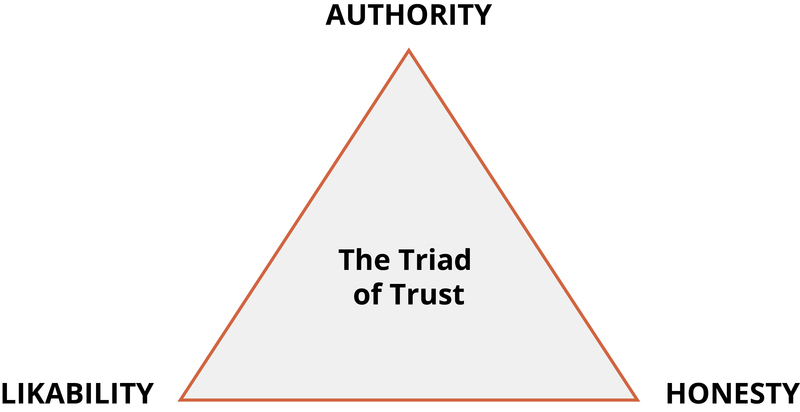
The Source of Persuasion: The Triad of Trustworthiness
Effective persuasion requires trusting the source of the communication. Studies have identified three characteristics that lead to trust: perceived authority, honesty, and likability.
When the source appears to have any or all of these characteristics, people not only are more willing to agree to their request but are willing to do so without carefully considering the facts. We assume we are on safe ground and are happy to shortcut the tedious process of informed decision making. As a result, we are more susceptible to messages and requests, no matter their particular content or how peripheral they may be.
Authority
From earliest childhood, we learn to rely on authority figures for sound decision making because their authority signifies status and power, as well as expertise. These two facets often work together. Authorities such as parents and teachers are not only our primary sources of wisdom while we grow up, but they control us and our access to the things we want. In addition, we have been taught to believe that respect for authority is a moral virtue. As adults, it is natural to transfer this respect to society’s designated authorities, such as judges, doctors, bosses, and religious leaders. We assume their positions give them special access to information and power. Usually we are correct, so that our willingness to defer to authorities becomes a convenient shortcut to sound decision making. Uncritical trust in authority may, however, lead to bad decisions. Perhaps the most famous study ever conducted in social psychology demonstrated that, when conditions were set up just so, two-thirds of a sample of psychologically normal men were willing to administer potentially lethal shocks to a stranger when an apparent authority in a laboratory coat ordered them to do so (Milgram, 1974; Burger, 2009).
Uncritical trust in authority can be problematic for several reasons. First, even if the source of the message is a legitimate, well-intentioned authority, they may not always be correct. Second, when respect for authority becomes mindless, expertise in one domain may be confused with expertise in general. To assume there is credibility when a successful actor promotes a cold remedy, or when a psychology professor offers his views about politics, can lead to problems. Third, the authority may not be legitimate. It is not difficult to fake a college degree or professional credential or to buy an official-looking badge or uniform.
Honesty
Honesty is the moral dimension of trustworthiness. Persuasion professionals have long understood how critical it is to their efforts. Marketers, for example, dedicate exorbitant resources to developing and maintaining an image of honesty. A trusted brand or company name becomes a mental shortcut for consumers. It is estimated that some 50,000 new products come out each year. Forrester Research, a marketing research company, calculates that children have seen almost six million ads by the age of 16. An established brand name helps us cut through this volume of information. It signals we are in safe territory. “The real suggestion to convey,” advertising leader Theodore MacManus observed in 1910, “is that the man manufacturing the product is an honest man, and the product is an honest product, to be preferred above all others” (Fox, 1997).
Likability

If we know that celebrities aren’t really experts, and that they are being paid to say what they’re saying, why do their endorsements sell so many products? Ultimately, it is because we like them. More than any single quality, we trust people we like. Roger Ailes, a public relations adviser to Presidents Reagan and George H.W. Bush, observed: “If you could master one element of personal communication that is more powerful than anything . . . it is the quality of being likable. I call it the magic bullet, because if your audience likes you, they’ll forgive just about everything else you do wrong. If they don’t like you, you can hit every rule right on target and it doesn’t matter.”
The mix of qualities that make a person likable are complex and often do not generalize from one situation to another. One clear finding, however, is that physically attractive people tend to be liked more. In fact, we prefer them to a disturbing extent: Various studies have shown we perceive attractive people as smarter, kinder, stronger, more successful, more socially skilled, better poised, better adjusted, more exciting, more nurturing, and, most important, of higher moral character. All of this is based on no other information than their physical appearance (e.g., Dion, Berscheid, & Walster, 1972).
Manipulating the Perception of Trustworthiness
The perception of trustworthiness is highly susceptible to manipulation. Levine (2003) lists some of the most common psychological strategies that are used to achieve this effect:
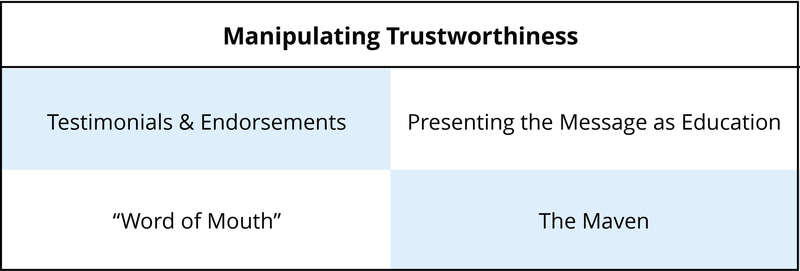
Testimonials and Endorsement
This technique employs someone who people already trust to testify about the product or message being sold. The technique goes back to the earliest days of advertising when satisfied customers might be shown describing how a patent medicine cured their life-long battle with “nerves” or how Dr. Scott’s Electric Hair Brush healed their baldness (“My hair (was) falling out, and I was rapidly becoming bald, but since using the brush a thick growth of hair has made its appearance, quite equal to that I had before previous to its falling out,” reported a satisfied customer in an 1884 ad for the product). Similarly, Kodak had Prince Henri D’Orleans and others endorse the superior quality of their camera (“The results are marvellous[sic]. The enlargements which you sent me are superb,“ stated Prince Henri D’Orleans in a 1888 ad).
Celebrity endorsements are a frequent feature in commercials aimed at children. The practice has aroused considerable ethical concern, and research shows the concern is warranted. In a study funded by the Federal Trade Commission, more than 400 children ages 8 to 14 were shown one of various commercials for a model racing set. Some of the commercials featured an endorsement from a famous race car driver, some included real racing footage, and others included neither. Children who watched the celebrity endorser not only preferred the toy cars more but were convinced the endorser was an expert about the toys. This held true for children of all ages. In addition, they believed the toy race cars were bigger, faster, and more complex than real race cars they saw on film. They were also less likely to believe the commercial was staged (Ross et al., 1984).
Presenting the Message as Education
The message may be framed as objective information. Salespeople, for example, may try to convey the impression they are less interested in selling a product than helping you make the best decision. The implicit message is that being informed is in everyone’s best interest, because they are confident that when you understand what their product has to offer that you will conclude it is the best choice. Levine (2003) describes how, during training for a job as a used car salesman, he was instructed: “If the customer tells you they do not want to be bothered by a salesperson, your response is ‘I’m not a salesperson, I’m a product consultant. I don’t give prices or negotiate with you. I’m simply here to show you our inventory and help you find a vehicle that will fit your needs.’”
Word of Mouth
Imagine you read an ad that claims a new restaurant has the best food in your city. Now, imagine a friend tells you this new restaurant has the best food in the city. Who are you more likely to believe? Surveys show we turn to people around us for many decisions. A 1995 poll found that 70% of Americans rely on personal advice when selecting a new doctor. The same poll found that 53% of moviegoers are influenced by the recommendation of a person they know. In another survey, 91% said they’re likely to use another person’s recommendation when making a major purchase.
Persuasion professionals may exploit these tendencies. Often, in fact, they pay for the surveys. Using this data, they may try to disguise their message as word of mouth from your peers. For example, Cornerstone Promotion, a leading marketing firm that advertises itself as under-the-radar marketing specialists, sometimes hires children to log into chat rooms and pretend to be fans of one of their clients or pays students to throw parties where they subtly circulate marketing material among their classmates.
The Maven
More persuasive yet, however, is to involve peers face-to-face. Rather than over-investing in formal advertising, businesses and organizations may plant seeds at the grassroots level hoping that consumers themselves will then spread the word to each other. The seeding process begins by identifying so-called information hubs—individuals the marketers believe can and will reach the most other people.
The seeds may be planted with established opinion leaders. Software companies, for example, give advance copies of new computer programs to professors they hope will recommend it to students and colleagues. Pharmaceutical companies regularly provide travel expenses and speaking fees to researchers willing to lecture to health professionals about the virtues of their drugs. Hotels give travel agents free weekends at their resorts in the hope they’ll later recommend them to clients seeking advice.
There is a Yiddish word, maven, which refers to a person who’s an expert or a connoisseur, as in a friend who knows where to get the best price on a sofa or the co-worker you can turn to for advice about where to buy a computer. They (a) know a lot of people, (b) communicate a great deal with people, (c) are more likely than others to be asked for their opinions, and (d) enjoy spreading the word about what they know and think. Most important of all, they are trusted. As a result, mavens are often targeted by persuasion professionals to help spread their message.
Other Tricks of Persuasion
There are many other mindless, mental shortcuts—heuristics and fixed action patterns—that leave us susceptible to persuasion. A few examples:
- "Free Gifts" & Reciprocity
- Social Proof
- Getting a Foot-in-the-Door
- A Door-in-the-Face
- "And That's Not All"
- The Sunk Cost Trap
- Scarcity & Psychological Reactance
Reciprocity
“There is no duty more indispensable than that of returning a kindness,” wrote Cicero. Humans are motivated by a sense of equity and fairness. When someone does something for us or gives us something, we feel obligated to return the favor in kind. It triggers one of the most powerful of social norms, the reciprocity rule, whereby we feel compelled to repay, in equitable value, what another person has given to us.
Gouldner (1960), in his seminal study of the reciprocity rule, found it appears in every culture. It lays the basis for virtually every type of social relationship, from the legalities of business arrangements to the subtle exchanges within a romance. A salesperson may offer free gifts, concessions, or their valuable time in order to get us to do something for them in return. For example, if a colleague helps you when you’re busy with a project, you might feel obliged to support her ideas for improving team processes. You might decide to buy more from a supplier if they have offered you an aggressive discount. Or, you might give money to a charity fundraiser who has given you a flower in the street (Cialdini, 2008; Levine, 2003).
Social Proof
If everyone is doing it, it must be right. People are more likely to work late if others on their team are doing the same, to put a tip in a jar that already contains money, or eat in a restaurant that is busy. This principle derives from two extremely powerful social forces—social comparison and conformity. We compare our behavior to what others are doing and, if there is a discrepancy between the other person and ourselves, we feel pressure to change (Cialdini, 2008).

The principle of social proof is so common that it easily passes unnoticed. Advertisements, for example, often consist of little more than attractive social models appealing to our desire to be one of the group. For example, the German candy company Haribo suggests that when you purchase their products you are joining a larger society of satisfied customers: “Kids and grown-ups love it so-- the happy world of Haribo”. Sometimes social cues are presented with such specificity that it is as if the target is being manipulated by a puppeteer—for example, the laugh tracks on situation comedies that instruct one not only when to laugh but how to laugh. Studies find these techniques work. Fuller and Skeehy-Skeffington (1974), for example, found that audiences laughed longer and more when a laugh track accompanied the show than when it did not, even though respondents knew the laughs they heard were connived by a technician from old tapes that had nothing to do with the show they were watching. People are particularly susceptible to social proof (a) when they are feeling uncertain, and (b) if the people in the comparison group seem to be similar to ourselves. As P.T. Barnum once said, “Nothing draws a crowd like a crowd.”
Commitment and Consistency
Westerners have a desire to both feel and be perceived to act consistently. Once we have made an initial commitment, it is more likely that we will agree to subsequent commitments that follow from the first. Knowing this, a clever persuasion artist might induce someone to agree to a difficult-to-refuse small request and follow this with progressively larger requests that were his target from the beginning. The process is known as getting a foot in the door and then slowly escalating the commitments.
Paradoxically, we are less likely to say “No” to a large request than we are to a small request when it follows this pattern. This can have costly consequences. Levine (2003), for example, found ex-cult members tend to agree with the statement: “Nobody ever joins a cult. They just postpone the decision to leave.”
A Door in the Face
Some techniques bring a paradoxical approach to the escalation sequence by pushing a request to or beyond its acceptable limit and then backing off. In the door-in-the-face (sometimes called the reject-then-compromise) procedure, the persuader begins with a large request they expect will be rejected. They want the door to be slammed in their face. Looking forlorn, they now follow this with a smaller request, which, unknown to the customer, was their target all along.
In one study, for example, Mowen and Cialdini (1980), posing as representatives of the fictitious “California Mutual Insurance Co.,” asked university students walking on campus if they’d be willing to fill out a survey about safety in the home or dorm. The survey, students were told, would take about 15 minutes. Not surprisingly, most of the students declined—only one out of four complied with the request. In another condition, however, the researchers door-in-the-faced them by beginning with a much larger request. “The survey takes about two hours,” students were told. Then, after the subject declined to participate, the experimenters retreated to the target request: “. . . look, one part of the survey is particularly important and is fairly short. It will take only 15 minutes to administer.” Almost twice as many now complied.
And That’s Not All!
The that’s-not-all technique also begins with the salesperson asking a high price. This is followed by several seconds’ pause during which the customer is kept from responding. The salesperson then offers a better deal by either lowering the price or adding a bonus product. That’s-not-all is a variation on door-in-the-face. Whereas the latter begins with a request that will be rejected, however, that’s-not-all gains its influence by putting the customer on the fence, allowing them to waver and then offering them a comfortable way off.
Burger (1986) demonstrated the technique in a series of field experiments. In one study, for example, an experimenter-salesman told customers at a student bake sale that cupcakes cost 75 cents. As this price was announced, another salesman held up his hand and said, “Wait a second,” briefly consulted with the first salesman, and then announced (“that’s-not-all”) that the price today included two cookies. In a control condition, customers were offered the cupcake and two cookies as a package for 75 cents right at the onset. The bonus worked magic: Almost twice as many people bought cupcakes in the that’s-not-all condition (73%) than in the control group (40%).
The Sunk Cost Trap
Sunk cost is a term used in economics referring to nonrecoverable investments of time or money. The trap occurs when a person’s aversion to loss impels them to throw good money after bad, because they don’t want to waste their earlier investment. This is vulnerable to manipulation. The more time and energy a cult recruit can be persuaded to spend with the group, the more “invested” they will feel, and, consequently, the more of a loss it will feel to leave that group. Consider the advice of billionaire investor Warren Buffet: “When you find yourself in a hole, the best thing you can do is stop digging” (Levine, 2003).
Scarcity and Psychological Reactance

People tend to perceive things as more attractive when their availability is limited, or when they stand to lose the opportunity to acquire them on favorable terms (Cialdini, 2008). Anyone who has encountered a willful child is familiar with this principle. In a classic study, Brehm & Weinraub (1977), for example, placed 2-year-old boys in a room with a pair of equally attractive toys. One of the toys was placed next to a plexiglass wall; the other was set behind the plexiglass. For some boys, the wall was 1 foot high, which allowed the boys to easily reach over and touch the distant toy. Given this easy access, they showed no particular preference for one toy or the other. For other boys, however, the wall was a formidable 2 feet high, which required them to walk around the barrier to touch the toy. When confronted with this wall of inaccessibility, the boys headed directly for the forbidden fruit, touching it three times as quickly as the accessible toy.
Research shows that much of that 2-year-old remains in adults, too. People resent being controlled. When a person seems too pushy, we get suspicious, annoyed, often angry, and yearn to retain our freedom of choice more than before. Brehm (1966) labeled this the principle of psychological reactance.
The most effective way to circumvent psychological reactance is to first get a foot in the door and then escalate the demands so gradually that there is seemingly nothing to react against. Hassan (1988), who spent many years as a higher-up in the “Moonies” cult, describes how they would shape behaviors subtly at first, then more forcefully. The material that would make up the new identity of a recruit was doled out gradually, piece by piece, only as fast as the person was deemed ready to assimilate it. The rule of thumb was to “tell him only what he can accept.” He continues: “Don’t sell them [the converts] more than they can handle . . . . If a recruit started getting angry because he was learning too much about us, the person working on him would back off and let another member move in .....”
Defending Against Unwelcome Persuasion
The most commonly used approach to help people defend against unwanted persuasion is known as the “inoculation” method. Research has shown that people who are subjected to weak versions of a persuasive message are less vulnerable to stronger versions later on, in much the same way that being exposed to small doses of a virus immunizes you against full-blown attacks. In a classic study by McGuire (1964), subjects were asked to state their opinion on an issue. They were then mildly attacked for their position and then given an opportunity to refute the attack. When later confronted by a powerful argument against their initial opinion, these subjects were more resistant than were a control group. In effect, they developed defenses that rendered them immune.
Sagarin and his colleagues have developed a more aggressive version of this technique that they refer to as “stinging” (Sagarin, Cialdini, Rice, & Serna, 2002). Their studies focused on the popular advertising tactic whereby well-known authority figures are employed to sell products they know nothing about, for example, ads showing a famous astronaut pontificating on Rolex watches. In a first experiment, they found that simply forewarning people about the deviousness of these ads had little effect on peoples’ inclination to buy the product later. Next, they stung the subjects. This time, they were immediately confronted with their gullibility. “Take a look at your answer to the first question. Did you find the ad to be even somewhat convincing? If so, then you got fooled. ... Take a look at your answer to the second question. Did you notice that this ‘stockbroker’ was a fake?” They were then asked to evaluate a new set of ads. The sting worked. These subjects were not only more likely to recognize the manipulativeness of deceptive ads; they were also less likely to be persuaded by them.
Anti-vulnerability trainings such as these can be helpful. Ultimately, however, the most effective defense against unwanted persuasion is to accept just how vulnerable we are. One must, first, accept that it is normal to be vulnerable and, second, to learn to recognize the danger signs when we are falling prey. To be forewarned is to be forearmed.
Conclusion
This module has provided a brief introduction to the psychological processes and subsequent “tricks” involved in persuasion. It has emphasized the peripheral route of persuasion because this is when we are most vulnerable to psychological manipulation. These vulnerabilities are side effects of “normal” and usually adaptive psychological processes. Mindless heuristics offer shortcuts for coping with a hopelessly complicated world. They are necessities for human survival. All, however, underscore the dangers that accompany any mindless thinking.
Outside Resources
- Book: Ariely, D. (2008). Predictably irrational. New York, NY: Harper.
- Book: Cialdini, R. B. (2008). Influence: Science and practice (5th ed.). Boston, MA: Allyn and Bacon.
- Book: Gass, R., & Seiter, J. (2010). Persuasion, social influence, and compliance gaining (4th ed.). Boston, MA: Pearson.
- Book: Kahneman, D. (2012). Thinking fast and slow. New York, NY: Farrar, Straus & Giroux.
- Book: Levine, R. (2006). The power of persuasion: how we\'re bought and sold. Hoboken, NJ: Wiley
- www.amazon.com/The-Power-Pers.../dp/0471763179
- Book: Tavris, C., & Aronson, E. (2011). Mistakes were made (but not by me). New York, NY: Farrar, Straus & Giroux.
- Student Video 1: Kyle Ball and Brandon Do's 'Principles of Persuasion'. This is a student-made video highlighting 6 key principles of persuasion that we encounter in our everyday lives. It was one of the winning entries in the 2015 Noba Student Video Award.
- Student Video 2: 'Persuasion', created by Jake Teeny and Ben Oliveto, compares the central and peripheral routes to persuasion and also looks at how techniques of persuasion such as Scarcity and Social Proof influence our consumer choices. It was one of the winning entries in the 2015 Noba Student Video Award.
- Student Video 3: 'Persuasion in Advertising' is a humorous look at the techniques used by companies to try to convince us to buy their products. The video was created by the team of Edward Puckering, Chris Cameron, and Kevin Smith. It was one of the winning entries in the 2015 Noba Student Video Award.
- Video: A brief, entertaining interview with the celebrity pickpocket shows how easily we can be fooled. See A Pickpocket’s Tale at
- http://www.newyorker.com/online/blogs/culture/2013/01/video-the-art-of-pickpocketing.html
- Video: Cults employ extreme versions of many of the principles in this module. An excellent documentary tracing the history of the Jonestown cult is the PBS “American Experience” production, Jonestown: The Life and Death of Peoples Temple at
- www.pbs.org/wgbh/americanexpe...-introduction/
- Video: Philip Zimbardo’s now-classic video, Quiet Rage, offers a powerful, insightful description of his famous Stanford prison study
- www.prisonexp.org/documentary.htm
- Video: The documentary Outfoxed provides an excellent example of how persuasion can be masked as news and education.
- http://www.outfoxed.org/
- Video: The video, The Science of Countering Terrorism: Psychological Perspectives, a talk by psychologist Fathali Moghaddam, is an excellent introduction to the process of terrorist recruitment and thinking
- sciencestage.com/v/32330/fath...spectives.html
Discussion Questions
- Imagine you are commissioned to create an ad to sell a new beer. Can you give an example of an ad that would rely on the central route? Can you give an example of an ad that would rely on the peripheral route?
- The reciprocity principle can be exploited in obvious ways, such as giving a customer a free sample of a product. Can you give an example of a less obvious way it might be exploited? What is a less obvious way that a cult leader might use it to get someone under his or her grip?
- Which “trick” in this module are you, personally, most prone to? Give a personal example of this. How might you have avoided it?
Vocabulary
- Central route to persuasion
- Persuasion that employs direct, relevant, logical messages.
- Fixed action patterns (FAPs)
- Sequences of behavior that occur in exactly the same fashion, in exactly the same order, every time they are elicited.
- Foot in the door
- Obtaining a small, initial commitment.
- Gradually escalating commitments
- A pattern of small, progressively escalating demands is less likely to be rejected than a single large demand made all at once.
- Heuristics
- Mental shortcuts that enable people to make decisions and solve problems quickly and efficiently.
- Peripheral route to persuasion
- Persuasion that relies on superficial cues that have little to do with logic.
- Psychological reactance
- A reaction to people, rules, requirements, or offerings that are perceived to limit freedoms.
- Social proof
- The mental shortcut based on the assumption that, if everyone is doing it, it must be right.
- The norm of reciprocity
- The normative pressure to repay, in equitable value, what another person has given to us.
- The rule of scarcity
- People tend to perceive things as more attractive when their availability is limited, or when they stand to lose the opportunity to acquire them on favorable terms.
- The triad of trust
- We are most vulnerable to persuasion when the source is perceived as an authority, as honest and likable.
- Trigger features
- Specific, sometimes minute, aspects of a situation that activate fixed action patterns.
References
- Barrett, D. (2010). Supernormal stimuli: How primal urges overran their evolutionary purpose. New York, NY: W.W. Norton.
- Brehm, J. W. (1966). A theory of psychological reactance. New York, NY: Academic Press.
- Brehm, S. S., & Weinraub, M. (1977). Physical barriers and psychological reactance: Two-year-olds’ responses to threats to freedom. Journal of Personality and Social Psychology, 35, 830–836.
- Burger, J. M. (2009). Replicating Milgram: Would people still obey today? American Psychologist, 64(1), 1–11.
- Burger, J. M. (1986). Increasing compliance by improving the deal: The that’s-not-all technique. Journal of Personality and Social Psychology, 51, 277–283.
- Cialdini, R. B. (2008). Influence: Science and practice (5th ed.). Boston, MA: Allyn and Bacon.
- Dion, K., Berscheid, E., & Walster, E. (1972). What is beautiful is good. Journal of Personality and Social Psychology, 24, 285–290
- Fox, Stephen (1997). The mirror makers: A history of American advertising and its creators. Champaign, IL: University of Illinois Press.
- Fuller, R. G., & Sheehy-Skeffington, A. (1974). Effects of group laughter on responses to humorous materials: A replication and extension. Psychological Reports, 35, 531–534.
- Gouldner, A. W. (1960). The norm of reciprocity: A preliminary statement. American Sociological Review, 25, 161–178.
- Hassan, S. (1988). Combating cult mind control. Rochester, VT: Park Street Press.
- Levine, R. (2003). The power of persuasion: How we’re bought and sold. Hoboken, NJ: Wiley.
- Levine, R. (2003). The power of persuasion: How we're bought and sold. Hoboken, NJ: John Wiley & Sons
- McGuire, W. (1964). Inducing resistance to persuasion: Some contemporary approaches. In L. Berkowitz (Ed.), Advances in experimental social psychology (Vol. 1, p. 306). New York, NY: Academic Press.
- Milgram, S. (1974). Obedience to authority: An experimental view. New York, NY: Harper & Row.
- Mowen, J. C., & Cialdini, R. B. (1980). On implementing the door-in-the-face compliance technique in a business context. Journal of Marketing Research, 17, 253–258.
- Myers, David (2011). Social psychology (10th ed.). New York, NY: Worth.
- Petty, R. E., & Cacioppo, J. T. (1986). The elaboration likelihood model of persuasion. In L. Berkowitz (Ed.), Advances in experimental social psychology (Vol. 19, pp. 123–205). San Diego, CA: Academic Press.
- Ross, R. P., Campbell, T., Wright, J. C., Huston, A. C., Rice, M. L., & Turk, P. (1984). When celebrities talk, children listen: An experimental analysis of children’s responses to TV ads with celebrity endorsement. Journal of Applied Developmental Psychology, 5, 185–202.
- Sagarin, B. J., Cialdini, R. B., Rice, W. E., & Serna, S. B. (2002). Dispelling the illusion of invulnerability: The motivations and mechanisms of resistance to persuasion. Journal of Personality and Social Psychology, 83, 526–541.


