1.10: Anonymous Routing
- Last updated
- Save as PDF
- Page ID
- 125596
What You’ll Learn
- Who has access to what on the internet
- Technologies that allow for anonymous communications online
- What anonymity is and the pitfalls of anonymity
In order to communicate online, packets of information need to be addressed to your computer, whether that information is from an instant-message conversation, an email, or browsing the web. In this section, we mostly focus on web browsing, although the same ideas apply in most settings. Your computer’s address, or IP address, is how internet communications reach your computer in the same way as a mailing address allows an envelope or package to reach your mailbox. For that reason, your computer’s current IP address (which changes depending on where you are connecting to the internet) is related to your physical location. How refined that physical location is depends on how much information the internet service provider (ISP) reveals and to whom they are willing to reveal it. The ISP knows which cable, phone line, or cell tower you are receiving internet traffic through but may only provide zip code information to the proliferation of IP geolocation websites. Or they may provide the location of a specific house.
Your IP address is just one piece of metadata that is necessary in order to get information to your computer. When browsing the web, though, a lot of other metadata, while not strictly necessary, is transmitted to “maximize your browsing experience.” This information includes details such as what browser plug-ins you use, your time zone, and your screen size and can be used as a unique identifier across IP addresses that you use to connect to the internet.
Who has access to all this metadata that can be used to identify you? Without encryption, such as using https, any eavesdropper would have access to this metadata as well as the content of your communications. Encryptions will protect some metadata from your ISP and eavesdroppers (such as which browser you are using) but not your IP address and not the web domains you are visiting. And the servers of the websites you are visiting will have access to your metadata as well as any content.
But since metadata is used to get information to you, is there any way to protect this metadata, and who could you protect it from? We describe two ways to anonymize your web browsing.
Trusting a Middle Man: Virtual Private Networks
Virtual private network (VPN) technology began as a means to extend a local network (such as a university’s or company’s network) to remote locations (such as off-campus housing and home offices) so that no matter where you were, you could access the same resources as you would if you were on the local networks (such as library and software subscriptions). While connected to a VPN, a web page host will see the IP address of the local network the VPN is extending as your address, the IP address of your home. For this reason, VPN use has become popular for anonymizing your location.
A VPN operates as a (hopefully benign) middle man (illustrated below). Rather than sending all her web requests directly, Assata sends all her web requests to her VPN, the VPN fetches her request from the internet for her, and then the VPN sends the results back to Assata. The specifics of how this is done vary between different VPN services, but generally, the communications between you and the VPN are encrypted. The protective quality of a VPN relies on many other people also connecting to that VPN. An eavesdropper looking at communications to and from the VPN will be able to identify the individuals connecting to the VPN and the web requests the VPN is fetching but ideally will be unable to match those web requests with the corresponding users because there are too many simultaneous requests in and out of the VPN.
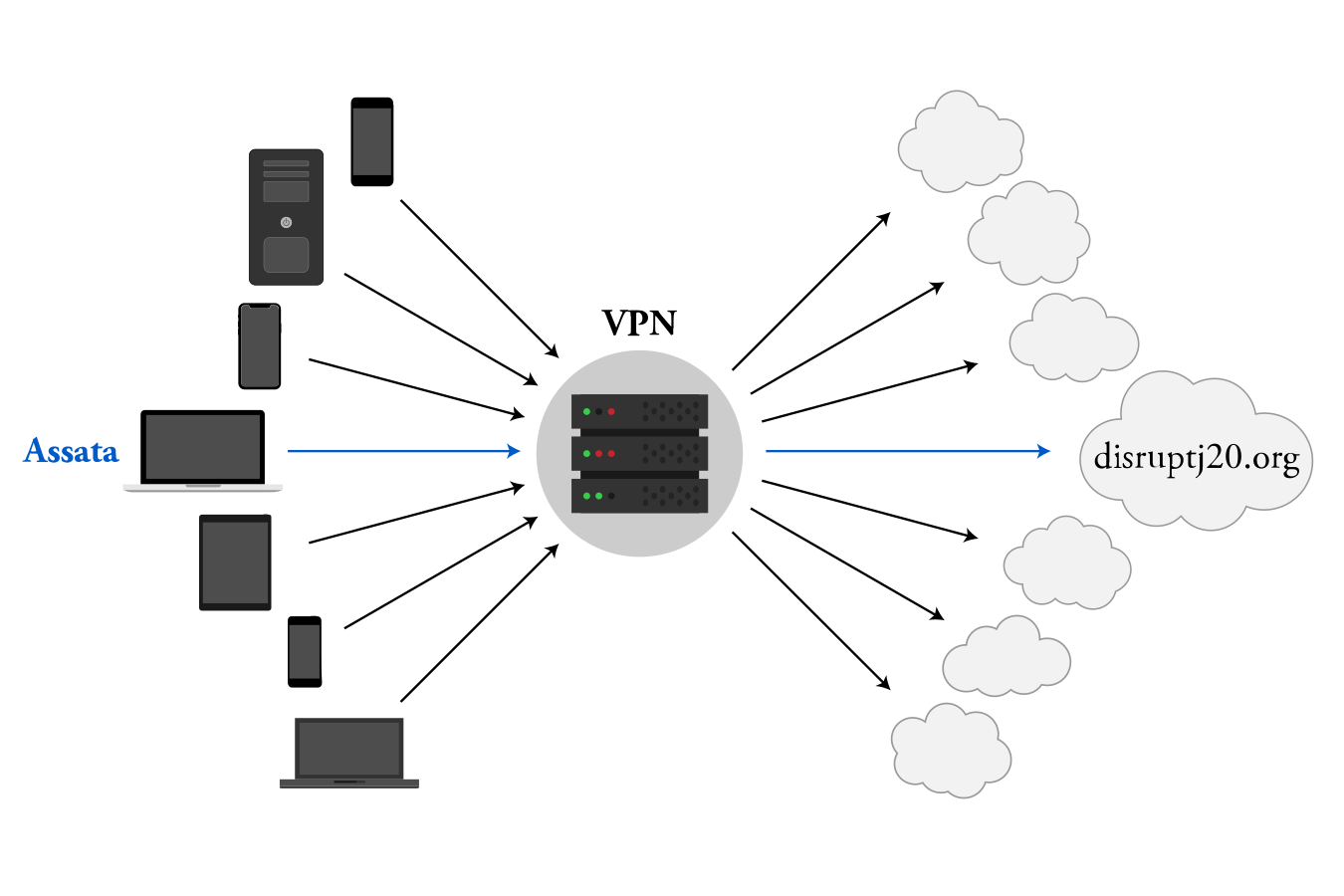
Of course, the VPN provider knows all your internet behavior, and with their cooperation, an adversary would too: you are trusting your VPN provider with that information. However, your ISP (without using a VPN) has access to the same information: you are putting the same trust in your VPN provider as you must in your ISP. The difference is that your ISP does not conceal your IP address from destination servers on the internet, while a VPN does. Some increased privacy risk, however, comes with using the same VPN across many connection locations (e.g., home, work, coffee shop), giving a single entity (that VPN) a more complete view of your internet use than available to the ISP at each location.
Not Trusting the Middle Man: The Onion Router
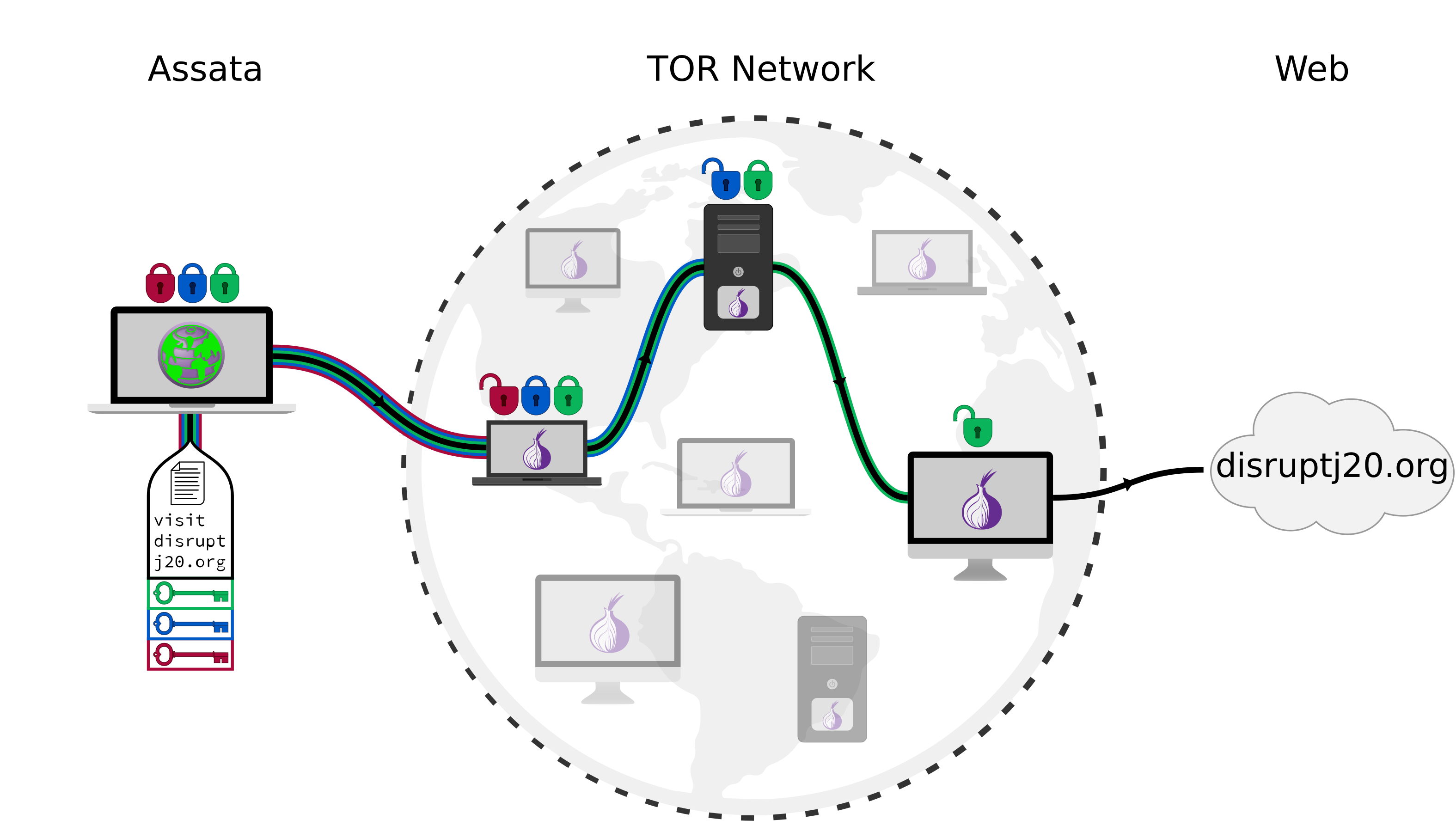
The Onion Router, or Tor, is a means of accessing the internet anonymously while sidestepping trust issues and gets its name from using layers of encryption (like the layers of an onion). Rather than using one middle man with whom you trust all your information, you use (at least) three intermediaries, chosen at random from a selection of thousands of volunteer servers (illustrated below). Traffic through this path of intermediaries is encrypted so that the first (entry) node only knows that you are accessing the internet via Tor, the second (relay) node only knows that someone is accessing something on the internet via Tor (but not who specifically or what specifically), and the last (exit) node only knows that a certain web page (for example) is being requested by a Tor user (but not which Tor user).
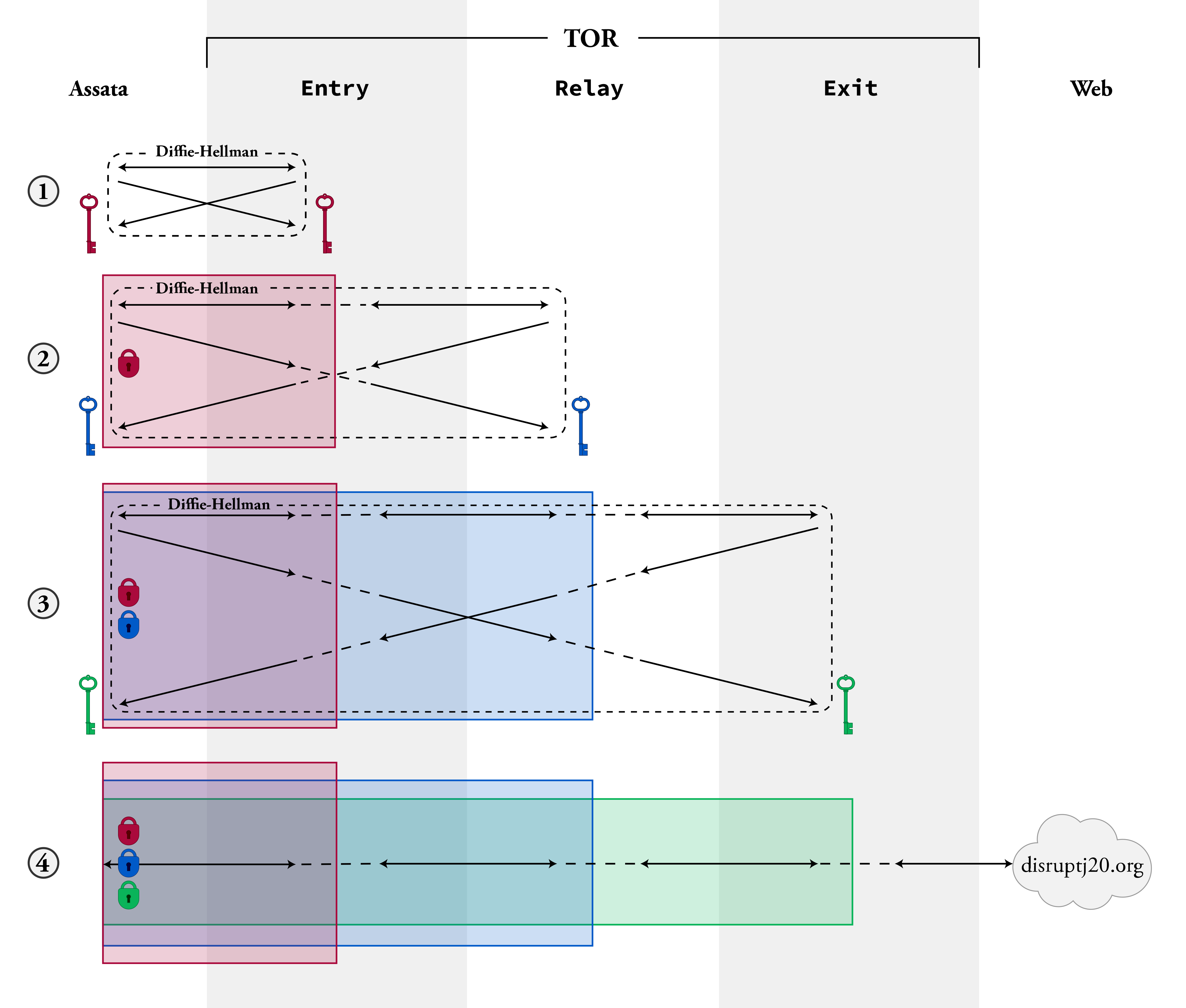
The way this is done is by Diffie-Hellman key exchanges first with the entry node, then with the relay node, and finally with the exit node as follows (and illustrated below). (1) Assata establishes a cryptographic key that she shares with the entry node (which we will call the entry key, in red). This establishes an encrypted communication channel between Assata and the entry node. (2) Assata uses this encrypted channel to communicate with the relay node via the entry node. The traffic between the entry and relay nodes is not encrypted, but Assata uses the channel via the entry node to establish a cryptographic key that Assata shares with the relay node (the relay key, in blue). All that the relay node knows is that it is setting up a shared key with some Tor user but not the identity of that Tor user. (3) This process is repeated to establish an encryption key that Assata shares with the exit node (the exit key, in green). (4) This created a sequence of keys (red, blue, green) that allow for encryption between Assata and the entry, relay, and exit nodes, respectively.
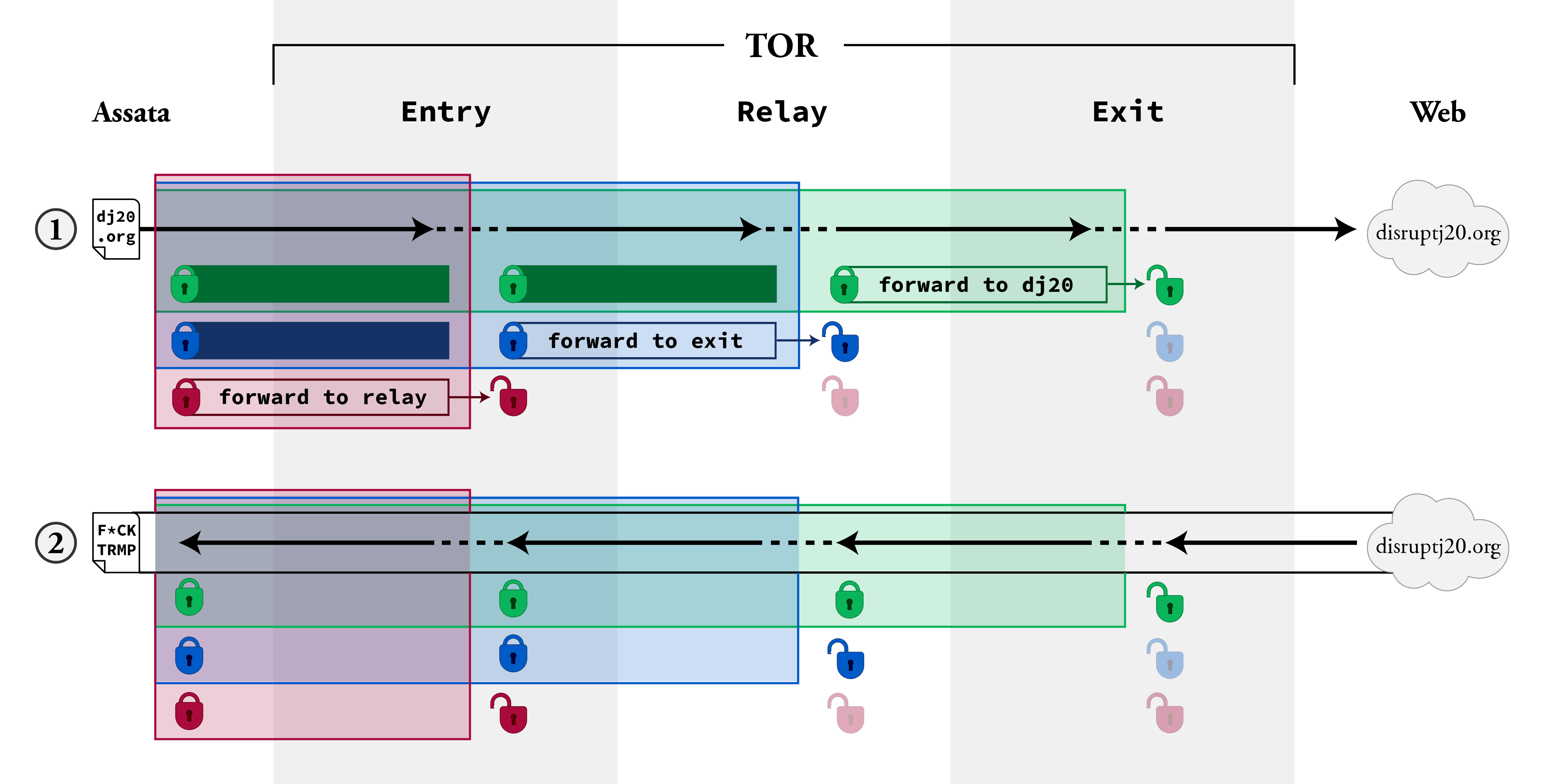
For Assata to send a request to disruptj20.org, she encrypts the request, addressed to disruptj20.org, with the green key and addresses this to the exit node; she wraps this in a message addressed to the relay node and encrypts this with the blue key; she wraps this in a message addressed to the entry node and encrypts this with the red key. The message is sent to the red node. The first layer of encryption is removed by the entry node (with the red key that the entry node shares with Assata), revealing a message addressed to the relay node. The second layer of encryption is removed by the relay node (with the blue key that the relay node shares with Assata), revealing a message addressed to the exit node. The third layer of encryption is removed by the exit node (with the green key that the exit node shares with Assata), revealing a message addressed to disruptj20.org, which the exit node forwards along. This is illustrated below (1).
For disruptj20.org to send information back to Assata, the web server sends the information back to the exit node. The exit node encrypts with the green key and sends it to the relay node. The relay node encrypts with the blue key and sends it to the entry node. The entry node encrypts with the red key and sends it to Assata. Assata can remove all three layers of encryption because she has all the necessary keys. This is illustrated below (2).
In order to re-create your path through the Tor network and therefore your web request, your adversary would need to control all three nodes that you select as your entry, relay, and exit nodes. Even an adversary who controls 80 percent of the Tor network would only have a 50 percent chance of controlling all three nodes that you select. Since there are thousands of Tor nodes (that anyone can volunteer to operate), this is unlikely.
An alternate attack that an adversary could take would be a confirmation attack. In this scenario, the adversary is trying to prove that you have visited a particular web service. If they can access your web traffic (e.g., through your ISP) and the web traffic of the target web service (through legal or extralegal means), then your adversary may be able to match up your use of Tor to access the web service from Tor based on their timing. This type of correlation was used in the case against Jeremy Hammond, convicted for hacking activities conducted by the activist collective Anonymous.
Other attacks have been made on Tor too, but the Tor project is very responsive to improving their technology and security. We discuss obstacles to anonymous browsing below and pitfalls a user may run into as well as best practices when trying to access the web anonymously in the chapter “Protecting Your Identity.”
Use and Prevention of Anonymous Browsing Technologies
Many people in countries where censorship of the internet is common, such as China and Iran, use VPNs and Tor to access the uncensored web. On the other hand, evidence of VPN traffic can be gleaned from the metadata of internet communications, and governments can use this to block all such communications, as has been done in China and Syria in their censorship efforts. Other countries, such as Iran, are known for blocking access to specific VPN providers that are not sanctioned by the government.
Tor as a whole can be blocked from use (e.g., by a government), since Tor nodes are publicly listed. This is done by simply blocking all traffic addressed to the Tor nodes. This is overcome by the use of bridges, a set of Tor nodes that are not publicly listed, which you use in lieu of a publicly listed entry node. To get access to a small set of bridge nodes, you need to email the Tor project from a restricted email account (e.g., Google, Riseup!, or Yahoo!) to request one. Tor can also be blocked by packet inspection—that is, by looking at the metadata of the communications (as with VPN traffic). The Tor project makes this process challenging by using methods of obfuscating Tor internet traffic so that it doesn’t look like Tor traffic.
VPN and Tor are also used to gain access to particular sites that might not be available in your jurisdiction because of a choice of the web host. This is common for many media platforms such as Hulu and Netflix. To this end, companies will often block access to content from known VPN service providers or from Tor exit nodes.
In Context: Disruptj20
On January 20, 2017, mass protests erupted around the inauguration of the forty-fifth president of the United States. Much of the organizing for those events was coordinated on the website disruptj20.org. In August 2017, it came to light that the US Department of Justice had issued a warrant to the disruptj20.org web host DreamHost requesting, among other items, “all HTTP request and error logs,” which would include the IP addresses of all individuals, purported to be 1.3 million people, who visited the website, along with which subpages they visited, how often they did so, and any text a visitor may have typed into the web page.
Of course, anonymous browsing technologies would have protected the IP addresses of visitors to that site.
What to Learn Next
- Protecting Your Identity
External Resources
- The Great Firewall of China keeps track of which and how many or how many times sites are censored in China.
- Search Warrant to DreamHost, August 2017.
Media Attributions
- anonymous-browsing-vpn © OSU OERU is licensed under a CC BY-NC (Attribution NonCommercial) license
- anonymous-browsing-tor © OSU OERU is licensed under a CC BY-NC (Attribution NonCommercial) license
- anonymous-browsing-TOR-1-keyexchange © OSU OERU is licensed under a CC BY-NC (Attribution NonCommercial) license
- anonymous-browsing-TOR-2-data-transfer © OSU OERU is licensed under a CC BY-NC (Attribution NonCommercial) license


